Wallet security and its corners
9 min read – Oct 20, 2022
Security is not a certainty.
Our core belief is that you should never treat security as certainty, and following this point of view will always put you ahead of potential problems.
Why should this be essential to you?
Technology, whether mechanical or information, is transitory, along with its security requirements. Security is part of technology and only lives as long as it suits the needs of its underlying application and accomplishes the desired result. What seems excellent for protecting your digital assets today may be redundant tomorrow. Security, in simple words, is buying time.
Metal gadgets
Metal devices are the first choice for protecting the keys; indeed, they are a good choice. Using metal plates or other types of metal gadgets is advertised as a top security approach everyone should opt for.
Durability is most often the selling point. As much as durability is significant, it is arguably not the most crucial protection aspect.
How important is durability compared to other types of risk, for example, losing your keys by being stolen?
Theft is an incomparably more common way of losing your assets than damage to the keys caused by fire or other natural causes (not undermining the importance of these causes). A thief can compromise your keys by taking a photo with a smartphone.
Preventing this can be challenging if your storage doesn’t have extra protection. As much as you cannot do anything to stop from capturing your keys, your focus should be to make access to your assets as complicated as possible. One way is obfuscating the keys, for example, by splitting them so that obtaining only the exposed portion would be meaningless.
Why wouldn’t the high melting point matter so much?
Passphrase
Along with using metal protections, many recommend using a passphrase. It is a very clever way to double-bet your security. A passphrase is supposed to prevent you from losing your digital assets when the keys have been compromised. If you are unfamiliar with this solution — it is an additional set of words to be appended to your seed. It often works as a disguised mechanism to distract potential thieves from the main assets. You set up the main wallet with a passphrase and another without a passphrase with an insignificant amount of digital assets to mislead the attacker.
The passphrase feature is great but has some serious caveats that often slip the attention during discussions.
Misusing it can be problematic at least and disastrous at most.
The often neglected fact is that it is very easy to make costly mistakes even if you are a tech and security-oriented individual.
Providing an incorrect phrase will never highlight a wrong entry, and it will most likely return an empty wallet, which can be a nerve-wracking experience.
The fundamental key to understanding a passphrase is that it is not a password and should never be handled like one. The critical difference between both is that the passphrase cannot be recovered!
Protecting your keys is already a complex job. Taking care of a passphrase with less attention often leads to poor security.
Always consider it as an integral part of your keys, and treat it with the same respect. Never keep the passphrase in proximity to your seed phrases. Do not use it if you don’t understand it. If you decide to use it, understand its benefits and disadvantages.
Using a passphrase requires great responsibility.
Here, our statement can be quite controversial; we would not push its usage for mass adoption. The particular reason for this is that mass adoption of the passphrase can lead to misusing it, and as a result, many may become victims of losing access to their wallets forever. You should use it only with a good security strategy, with a deep understanding of its limitations.
Multi-signatures
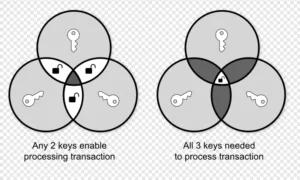 Multisig (abbreviation for Multi-signatures) is yet another method at your disposal. The concept is simple — it requires more than 1 participant to make a transaction; thus, this procedure relies heavily on trust between parties.
Multisig (abbreviation for Multi-signatures) is yet another method at your disposal. The concept is simple — it requires more than 1 participant to make a transaction; thus, this procedure relies heavily on trust between parties.
Each stakeholder keeps its private key, without whom the transaction cannot take place. With multi-signatures, you can set up threshold criteria — for example, you could mandate that 2 out of 3 stakeholders authorize the transaction in the wallet.
Another way can be without the threshold, where strict participants are required. This has one significant weakness —a single point of failure. All parties must be aware of this and have a good backup plan in place.
Where wouldn’t it be wise to use the multi-signature?
Perhaps in the setup where you need to rely heavily on other participants, particularly if they don’t have as extensive security knowledge as yourself. Especially try to avoid Multi-signatures without a threshold if you are not certain other parties can manage the keys. Using a multisig setup with your partner can also be problematic. Remember, you both need to take care of your own keys in the most disciplined manner in order to prevent limiting access to funds just in case one of you is no longer around.
Where would it make sense to use it?
Multi-signature with a threshold is perfect for organizations where decisions are made with the majority votes.
Paper
Back in the days when Cryptocurrencies were still a hobby, one of the ways to store the keys was by printing them on paper. Although not recommended by many, we would argue that this method is not pointless and still has robust utility.
The primary advantage is that paper is a cheap way to store your keys.
Of course, paper is a very delicate material. It can be damaged and lost quickly, its prints are not durable, and it doesn’t weigh the importance as much as dedicated gadgets. Moreover, it is easy to print too many and place them in unsecured locations.
We understand that you should avoid making security decisions based on costs. Ultimately, the price you pay for your system should not be the main deciding factor when trying to obtain maximum protection for your assets. It will likely play a significant role, often based on the value of the coins you are looking to protect.
We want to stress that our argument for using paper is not because it is cheap. Still, we see the opportunity to guide you to adopt our main principle of treating security not as a certainty but as a transient solution, where your job is continuously taking care of your setup.
One of the main dilemmas when using metal gadgets is, what should you do if your keys were compromised, yet a passphrase still protects them?
Should you re-evaluate your strategy and move your assets to a new wallet where you can obtain a new seed phrase? Are you confident to use the same wallet and that a passphrase is enough to secure your coins? In the end, the fabric of your security setup may be broken.
If you want to learn how to protect your keys with a paper backup, please read the following stories, where we highlight many essential points you should pay attention to.
 If you think to protect your recovery keys for your cryptocurrencies in the best way possible, we have created a dedicated application to help you achieve this. In this article, we will explain how our application works, and what benefits you can expect. Read more
If you think to protect your recovery keys for your cryptocurrencies in the best way possible, we have created a dedicated application to help you achieve this. In this article, we will explain how our application works, and what benefits you can expect. Read more  It is a no-brainer to say, that protecting your recovery keys is one of the first things you need to learn and understand when entering the crypto space.
Printing and distributing them into secured locations is the way many, if not most of us, do. Read more
It is a no-brainer to say, that protecting your recovery keys is one of the first things you need to learn and understand when entering the crypto space.
Printing and distributing them into secured locations is the way many, if not most of us, do. Read more